“You mean all we need to do to defeat him is adopt HTML5? Why didn’t you say?” Photo by Tom Simpson on Flickr.
A selection of 8 links for you. Uninflammable. I’m charlesarthur on Twitter. Observations and links welcome.
Encryption “would not have helped” at OPM, says DHS official » Ars Technica
Sean Gallagher:
pressed on why systems had not been protected with encryption prior to the recent discovery of an intrusion that gave attackers access to sensitive data on millions of government employees and government contractors, [US Office of Personnel Management Katherine Archuleta] said, “It is not feasible to implement on networks that are too old.” She added that the agency is now working to encrypt data within its networks.
But even if the systems had been encrypted, it likely wouldn’t have mattered. Department of Homeland Security Assistant Secretary for Cybersecurity Dr. Andy Ozment testified that encryption would “not have helped in this case” because the attackers had gained valid user credentials to the systems that they attacked—likely through social engineering. And because of the lack of multifactor authentication on these systems, the attackers would have been able to use those credentials at will to access systems from within and potentially even from outside the network…
…nearly every question of substance about the breach—which systems were affected, how many individuals’ data was exposed, what type of data was accessed, and the potential security implications of that data—was deferred by Archuleta on the grounds that the information was classified. What wasn’t classified was OPM’s horrible track record on security, which dates back at least to the George W. Bush administration—if not further.
Serious OS X and iOS flaws let hackers steal keychain, 1Password contents » Ars Technica
Dan Goodin:
The malicious proof-of-concept apps were approved by the Apple Store, which requires all qualifying submissions to treat every other app as untrusted. Despite the supposed vetting by Apple engineers, the researchers’ apps were able to bypass sandboxing protections that are supposed to prevent one app from accessing the credentials, contacts, and other resources belonging to another app. Like Linux, Android, Windows, and most other mainstream OSes, OS X and iOS strictly limit app access for the purpose of protecting them against malware. The success of the researchers’ cross-app resource access—or XARA—attacks, raises troubling doubts about those assurances on the widely used Apple platforms.
“The consequences are dire,” they wrote in a research paper titled Unauthorized Cross-App Resource Access on MAC OS X and iOS. “For example, on the latest Mac OS X 10.10.3, our sandboxed app successfully retrieved from the system’s keychain the passwords and secret tokens of iCloud, email and all kinds of social networks stored there by the system app Internet Accounts, and bank and Gmail passwords from Google Chrome.”…
…It’s not the first time researchers have found flaws in application sandboxes. The attack exploiting WebSocket weaknesses, for instance, can also succeed in Windows under certain conditions, the researchers said. Interestingly, they said application sandboxing in Google’s Android OS was much better at withstanding XARA threats.
For the time being, the researchers told Ars, there isn’t much end users can do except wait for Apple to fix the vulnerabilities.
Bad (though not deluge-of-malware bad; instead it’s sneaky-Trojan bad). Apple was told about this in October 2014. The best hope is that this is fixed in OS X 10.11 and iOS 9, but there’s no clear indication of how hard it is to fix.
Freedom of information turns into Mission Impossible for Downing St emails » FT.com
Jim Pickard and Kiran Stacey:
Emails sent from computers in Downing Street are automatically deleted within three months under a system that makes it harder for the public to obtain answers to “freedom of information” requests, former staff have disclosed.
The system, instigated a decade ago but not widely known about, means that messages are only held beyond that period if an individual saves them. It is widely blamed by government advisers for what one former employee called a sometimes “dysfunctional” operation at the heart of Whitehall.
The email system was introduced under the Labour government in late 2004, just weeks before January 2005 when the Freedom of Information Act belatedly came into force.
“The timing of this very strongly indicates that it was not a coincidence,” said Maurice Frankel, director of the UK Campaign for Freedom of Information.
Gee, ya think?
China and Russia almost definitely have the Snowden docs » WIRED
Bruce Schneier (who is a veritable security expert; if he says it, it’s true):
The vulnerability is not Snowden; it’s everyone who has access to the files.
First, the journalists working with the documents. I’ve handled some of the Snowden documents myself, and even though I’m a paranoid cryptographer, I know how difficult it is to maintain perfect security. It’s been open season on the computers of the journalists Snowden shared documents with since this story broke in July 2013. And while they have been taking extraordinary pains to secure those computers, it’s almost certainly not enough to keep out the world’s intelligence services…
…In general, it’s far easier to attack a network than it is to defend the same network. This isn’t a statement about willpower or budget; it’s how computer and network security work today. A former NSA deputy director recently said that if we were to score cyber the way we score soccer, the tally would be 462–456 twenty minutes into the game.
Even airgapped, never-connected computers can be attacked (don’t ask me how). The Guardian took extraordinary pains with its London copy: two people needed to enter passwords, at least two people needed to be present when documents were read, the computers used had never been online and had no connection.
But a simpler thought is this: if Snowden was one of 10,000 or so NSA staff with access to that data (and more in the UK), what are the chances that absolutely none of those has somehow been coerced or willingly turned over data to foreign powers? Pretty much zero.
Flash will soon be obsolete: it’s time for agencies to adapt » Advertising Age
David Evans on the fact that major browsers on desktop are hurrying to dump Flash:
If this sounds like a big problem to you, you’re absolutely right. If the major browsers were to disable Flash immediately, we could be looking at a scenario where roughly 84% of banners across the internet would not be viewable on desktop browsers. Rather than clicking on a visually dynamic, animated ad created to capture attention with movement and video, users would instead see a static banner in place of the intended ad, and most advertising creatives don’t pay much attention to the creation of static backups.
For advertisers, this could mean shelling out first-class money for economy-class impressions.
Though it might be painful to admit for an industry that has relied on Flash for over a decade, the right choice is to start creating desktop ads in the HTML5 language used to create ads for mobile.
This is a bit obvious to anyone who’s been paying attention for the past three years (minimum), but perhaps advertising has been looking somewhere else.
Market Monitor Q1 2015: LATAM smartphones grow 25% annually » Counterpoint Technology
Tina Lu:
LATAM is third, behind North America and Europe in the global ranking of smartphone shipment penetration.
• Except for Peru, majority of the key LATAM markets are seeing a significantly higher smartphone demand, with shipment penetration of total handsets between 77% and 99%.
• Overall feature phone demand has been declining, and so has been the overall scale and profitability of manufacturing and selling them. As a result, in countries like Argentina, due to government protectionist measures and import restrictions, vendors are manufacturing and selling only the more profitable smartphones. This has led to smartphone shipment penetration of sales to reach 99%; the highest in the region.
Here’s the shipment figure: 
If you do the maths, on a 25% yoy growth both Samsung’s and LG’s shipments actually fell; Apple’s more than doubled. Alcatel and “Others” both grew faster than the market.
Apple’s Siri, Spotlight extend Google-like search inside iOS 9 apps, without tracking users » Apple Insider
Daniel Eran Dilger:
Because Apple is indexing in-app content for its search results, it can more easily suppress “Search Engine Optimization” malicious content or link spamming, as relevancy is tied to user engagement. If few users find a search result worthwhile, it can fade from relevance.
Many of the new search-related features Apple debuted for iOS 9 and OS X El Capitan bear a strong resemblance to some of predictive search features first introduced by Google starting back in 2012 as part of Android 4.1, branded as “Google Now.”
Since then, Google has introduced “app indexing,” a related feature designed to make the company’s web-style search more relevant to mobile users by delivering results that can open within local apps. For example, a recipe might open within a cookbook app, rather than just presenting the same information on a web page or dumping users into the app to find the recipe on their own.
The most profound difference between the two companies’ approach to in-app search is that Apple does not monetize its search with ads, and therefore has no need to capture and store users’ data and behaviors for future profiling, tied to a persistent user and device identifier that individuals can’t easily remove.
Apple is perhaps two years behind Google on this – but most people are using a version of Android that is at least two years old (87% are using 4.4, KitKat, from November 2013, or earlier). Which means that by November or so, Apple will roughly have parity on this feature.
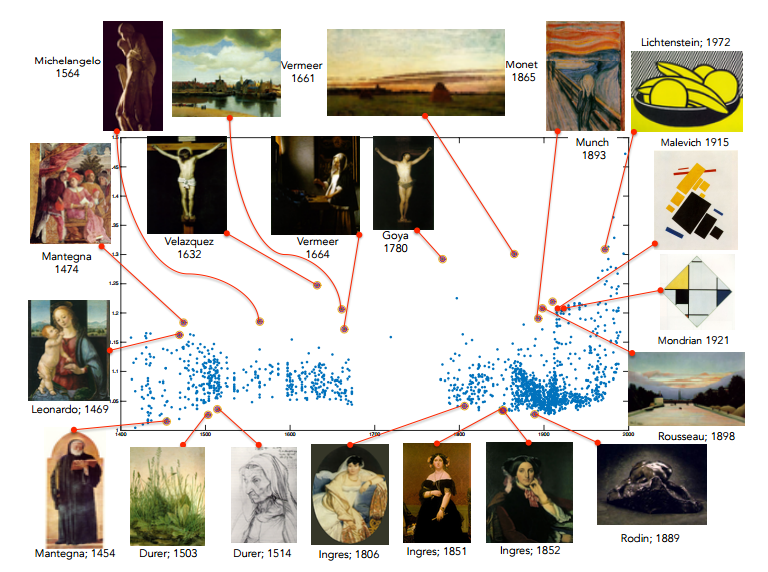
Machine vision algorithm chooses the most creative paintings in history » MIT Technology Review
The job of distinguishing the most creative from the others falls to art historians. And it is no easy task. It requires, at the very least, an encyclopedic knowledge of the history of art. The historian must then spot novel features and be able to recognize similar features in future paintings to determine their influence.
Those are tricky tasks for a human and until recently, it would have been unimaginable that a computer could take them on. But today that changes thanks to the work of Ahmed Elgammal and Babak Saleh at Rutgers University in New Jersey, who say they have a machine that can do just this.
They’ve put it to work on a database of some 62,000 pictures of fine art paintings to determine those that are the most creative in history. The results provide a new way to explore the history of art and the role that creativity has played in it.
Can’t be long before someone puts a human art historian up against the machine to see who spots the fake. (By the way, there was no byline I could find on the story. Maybe a robot wrote it.)