
Fast-forward ten years, and what will be in the phone Apple unveils? We already have clues. Photo by portalgda on Flickr.
You can now sign up to receive each day’s Start Up post by email. You’ll need to click a confirmation link, so no spam.
A selection of 10 links for you. The last of the month! I’m @charlesarthur on Twitter. Observations and links welcome.
Six things to know about Steve Ballmer, youth basketball coach • The Ringer
Zach Schwartz used to be on the year 3 (8-9 year-olds) basketball team in Bellevue, Washington state:
»
Steve went beyond helping us develop the basic fundamentals. He worked on our shooting form and was the first coach who had us running sprints after practice to ensure that we would be ready to finish strong in the fourth quarter. Steve took coaching seriously and even brought in an NBA shooting coach to help us with our form. Steve loved the team, and we loved playing for Steve. He was running one of the most successful companies on earth and still making time to coach us. He never missed one of our games. Our team was legendary within Microsoft circles because of the lengths that Steve would go to in making sure that he attended our games. He’d do a video interview on CNBC from China on a Friday, then take a red-eye back to the States and head straight to the gym to coach us.
«
It’s pretty easy to forget that people who have real drive spread that drive all through their life. Ballmer really is bigger than he appears. It would have been easy for him to shrug off some of the responsibility. He didn’t.
link to this extract
Twitter finds hundreds of accounts tied to Russian operatives • The Washington Post
Elizabeth Dwoskin, Adam Entous and Karoun Demirjian:
»
Twitter has shut down 201 accounts that were tied to the same Russian operatives who posted thousands of political ads on Facebook, the company told congressional investigators in a meeting Thursday and revealed in a blog in the afternoon.
The company also found three accounts from the news site RT — which Twitter linked to the Kremlin — that spent $274,100 in ads on Twitter’s platform in 2016.
The meeting between the company and Congressional investigators was part of a widening government probe into how Russian operatives used Facebook, Google, Twitter and other social media platforms to sow division and disinformation during the 2016 campaign. Those companies are under increasing pressure from Capitol Hill to investigate Russian meddling on their platforms and are facing the possibility of new regulations that could impact their massive advertising businesses.
Still, some lawmakers have raised questions over the tech industry grasps the serious nature of the problem.
Sen. Mark Warner (D-Va.) said Twitter’s presentation to a closed door meeting of lawmakers from the Senate and House was “deeply disappointing” and “inadequate on almost every level.”
«
Only 201? I’d have thought it would be about a thousand times more at least.
link to this extract
iPhone XX futurology • Medium
»
Ten years from now, in 2027, an Apple executive will once again grace the stage to show eager fans the new iPhone. This iPhone will be the 20th anniversary model with 20 years of improvements, refinements and technological achievements under its belt.
In this piece I’ll lay out what I believe this iPhone XX will look like and how it will fit into an accelerating future of technology.
This is not a sci-fi article. The iPhone of 2007 and the iPhone of 2017 look generally similar to one another, so let’s talk about some off-the-wall futuristic iPhone ideas and why I don’t believe we’ll be seeing them in 2027.
Why still a rectangle and not a square? Or a circle? First, books are not squares or circles, they’re rectangles. Humans read text on a page in a particular way and I believe a portrait screen ratio will be sticking around for at least the next ten years.
Why still think there will even be an iPhone? What about AR glasses and VR goggles and flying cars? Technology doesn’t move as fast as people think. 100 years ago people were convinced we’d be living in colonies on Mars and food would materialize from pills. Instead we haven’t put a person on a new celestial body in 50 years and Soylent not only tastes bad but made people sick. The iPhone will still be around in 2027 and will still mostly look like the smartphones we use today.
That’s not to say that VR goggles and AR glasses won’t exist in 10 years, they just won’t be replacing the devices in our pockets.
«
This is loooong but it’s all based on patents Apple has filed; ten years isn’t a long time in that timeframe. And previous patents pointed to how things would change.
link to this extract
1992: the executive computer – ‘mother of all markets’ or a ‘pipe dream driven by greed’? • NYTimes.com
»
“We are writing Chapter 2 of the history of personal computers,” said Nobuo Mii, vice president and general manager of the International Business Machines Corporation’s entry systems division.
How rich is this lode? At one end of the spectrum is John Sculley, the chief executive of Apple Computer Inc., who says these personal communicators could be “the mother of all markets.”
At the other end is Andrew Grove, the chairman of the Intel Corporation, the huge chip maker based in Santa Clara, Calif. He says the idea of a wireless personal communicator in every pocket is “a pipe dream driven by greed.”
These devices are expected to combine the best features of personal computers, facsimile machines, computer networks, pagers, personal secretaries, appointment books, address books and even paperback books and pocket CD players — all in a hand-held box operated by pen, or even voice commands.
Stuck in traffic on a business trip, an executive carrying a personal communicator could send and receive electronic mail and facsimile messages from anywhere in the country. She could also call up a local map on a 3-inch by 5-inch screen, draw a line between her current position (confirmed by satellite positioning signals) and her intended destination, and the device would give her specific driving instructions (as well as real-time warnings about traffic jams or accidents). Certainly, these are just predictions for now, but they sure are fun to think about.
«
I do hope you’re reading this on your personal communicator with a 3in by 5in screen while in traffic. The iPhone in particular was still 15 years away, but notice the difference in Apple’s and Intel’s view. This was, for most people, pre-internet too. Vision is difficult; patience to realise it, even more so.
link to this extract
February 1985: Playboy Interview: Steve Jobs • Longform
David Sheff interviewed Jobs in 1985, at a time when hardly anyone had touched a PC, and the internet was still an academic pursuit:
»
Playboy: Those are arguments for computers in business and in schools, but what about the home?
Jobs: So far, that’s more of a conceptual market than a real market. The primary reasons to buy a computer for your home now are that you want to do some business work at home or you want to run educational software for yourself or your children. If you can’t justify buying a computer for one of those two reasons, the only other possible reason is that you just want to be computer literate. You know there’s something going on, you don’t exactly know what it is, so you want to learn. This will change: Computers will be essential in most homes.
Playboy: What will change?
Jobs: The most compelling reason for most people to buy a computer for the home will be to link it into a nationwide communications network. We’re just in the beginning stages of what will be a truly remarkable breakthrough for most people—as remarkable as the telephone.
Playboy: Specifically, what kind of breakthrough are you talking about?
Jobs: I can only begin to speculate. We see that a lot in our industry: You don’t know exactly what’s going to result, but you know it’s something very big and very good.
«
Jobs was really good at describing big differences (mouse v keyboard: “If I want to tell you there is a spot on your shirt, I’m not going to do it linguistically: “There’s a spot on your shirt 14 centimeters down from the collar and three centimeters to the left of your button.” If you have a spot—“There!” [he points]—I’ll point to it. Pointing is a metaphor we all know.”) He was wise to give up the bow ties, though.
link to this extract
FCC demands Apple ‘put the safety of the American people first’, activate iPhone FM radio • 9to5Mac
»
FCC Chairman Pai’s statement comes on the same day as the NAB (via Bloomberg) similarly pushing for Apple to enable FM radio on iPhones:
»
“Broadcasters are providing information on how to evacuate quickly, where flood waters are raging, how to get out of harm’s way if there’s a tornado or a hurricane,” said Dennis Wharton, a spokesman for the National Association of Broadcasters. “The notion that Apple or anyone else would block this type of information is something that we find fairly troubling.”
«
While Apple isn’t commenting on the renewed requests, critics speculate that Apple’s thinking may be FM radio access would hurt its services business which includes Apple Music and streaming radio services over cellular.
In practice, FM radio access would likely still require a traditional antenna (the discontinued iPod nano featured FM radio access using the headphones as the antenna) and wouldn’t be as simple as just turning on the function.
«
Apple’s response: the iPhone 7 onwards don’t have FM radio chips or the antennae to receive FM signals “so it is not possible to enable FM reception in these products”. Seems like the FCC chair is prone to being clueless.
link to this extract
Emails show how an Ivy League prof tried to do damage control for his bogus food science • Buzzfeed
»
The Smarter Lunchrooms Movement, a $22m federally funded program that pushes healthy-eating strategies in almost 30,000 schools, is partly based on studies that contained flawed — or even missing — data.
The main scientist behind the work, Cornell University professor Brian Wansink, has made headlines for his research into the psychology of eating. His experiments have found, for example, that women who put cereal on their kitchen counters weigh more than those who don’t, and that people will pour more wine if they’re holding the glass than if it’s sitting on a table. Over the past two decades he’s written two popular books and more than 100 research papers, and enjoyed widespread media coverage (including on BuzzFeed).
Yet over the past year, Wansink and his “Food and Brand Lab” have come under fire from scientists and statisticians who’ve spotted all sorts of red flags — including data inconsistencies, mathematical impossibilities, errors, duplications, exaggerations, eyebrow-raising interpretations, and instances of self-plagiarism — in 50 of his studies.
Journals have so far retracted three of these papers and corrected at least seven. Now, emails obtained by BuzzFeed News through public information requests reveal for the first time that Wansink and his Cornell colleague David Just are also in the process of correcting yet another study, “Attractive names sustain increased vegetable intake in schools,” published in Preventive Medicine in 2012.
«
Who could have guessed that headline-friendly “science” might be flawed?
link to this extract
August 2001: One on one with Larry Page, CEO of Google • San Francisco Business Times
Lizette Wilson, back in August 2001, when the dot-com boom (remember that?) had turned to the ashes of the dot-com bust, yet Google was still standing:
»
Q: How do you come up with the relevancy search results?
LP: We use a whole bunch of techniques. We estimate the importance of the page, the font size, how close the words are together. We look at what other documents say about it at how good the links are. We probably do 30 such things like that.
Q: If you could make more money by doing paid placement in results, would you?
LP: No. We’d make money in the short term, but not the long term.
Q: How does advertising or “sponsored links” differ from paid placement in the eyes of the average user?
LP: It doesn’t and that’s the problem. We believe that advertising and editorial should be split. We do the best job we can with computers and such to give you best search result content. We don’t do pay for placement.
Q: Is that a moral stance or a business one?
LP: Both. We believe that the company that’s successful will be trusted. When people trust us, then we’ll make more money.
Q: What about advertising? Are you going after more of that revenue now?
LP: The sales part is fairly easy for us. We get a lot of incoming requests and generate a lot of incoming leads.
Q: Okay, what’s the hard part then?
It’s delivering amazing products for people and reading their minds and providing exactly what they want when they do a search.
«
Why Google’s auction-based proposal does not comply with EC remedy requirements • Foundem
This is an interactive HTML presentation (hooray! The web lives!) by Foundem, the original – and successful – complainant against Google over how shopping searches are ranked.
Google, as noted previously, has suggested that to comply with the EC complaint, it will split its shopping service off from the rest of the business and bid for auctioned-off shopping ad slots.
This obviously doesn’t make any difference, unless it were to completely sell it off from Alphabet. Google wins if Google Shopping doesn’t win an auction slot, because it gets the ad revenue; Google wins if Google Shopping does get the auction slot, because people may click through. Google wins.
But there doesn’t seem to be any way to slice this satisfactorily if Google can sell shopping ad slots – as long, that is, as it suppresses shopping searches in the “organic” search results.
link to this extract
Worldwide wearable device sales to grow 17% in 2017 • Gartner
»
Apple will continue to have the greatest market share of any smartwatch provider. However, as more providers enter the market, Apple’s market share will decrease from approximately a third in 2016 to a quarter in 2021. The announcement of a new Apple Watch expected in September may enable direct cellular connectivity for interacting with Siri, texting and transferring sensor data when the phone or Wi-Fi is not present.
We expect other consumer electronics brands such as Asus, Huawei, LG, Samsung and Sony to sell only 15% of smartwatches in 2021, because their brands do not have as strong an appeal as lifestyle brands for personal technologies.
Two sub-categories that Gartner expects to perform well are kids’ smartwatches and traditional watch brands, which will emerge as significant segments for smartwatches. Gartner expects kids’ smartwatches to represent 30% of total smartwatch unit shipments in 2021. These devices are targeted at children in the 2-to-13 year-old range, before parents provide them with a smartphone.
The other sub-category, which will account for 25% of smartwatch units by 2021, is fashion and traditional watch brands. “Luxury and fashion watch brands will offer smartwatches in an attempt to attract younger customers,” said Ms. McIntyre. A final sub-category is represented by the startup and white-label brands (e.g., Archos, Cogito, Compal, Martian, Omate or Quanta), which will account for 5% of smartwatch unit sales in 2021.
«
Gartner reckons the smartwatch market in 2021 will be 81m units – so if Apple has a quarter of it, that’s 20.3m units. Comparison now: Gartner expects all smartwatches will sell 41.5m units, and Apple has about a third – that’s 13.8m units. It’s growth, though hardly dramatic.
This analysis throws in everything, including Bluetooth headsets. Though note: “By 2021, we assume that almost all premium mobile phones will no longer have the 3.5 mm jack,” according to Angela McIntyre at Gartner.
Also, I wouldn’t expect many of the traditional Android OEMs still to be in the smartwatch market by 2021. Samsung yes, Huawei maybe. For the others, there’s too little volume.
link to this extract
Errata, corrigenda and ai no corrida: none notified




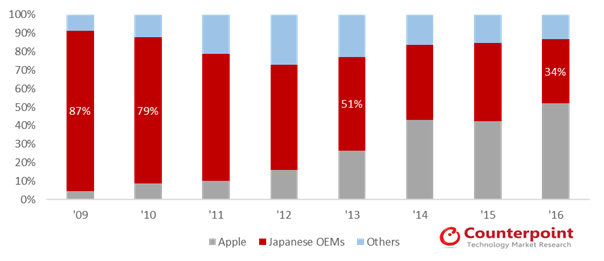
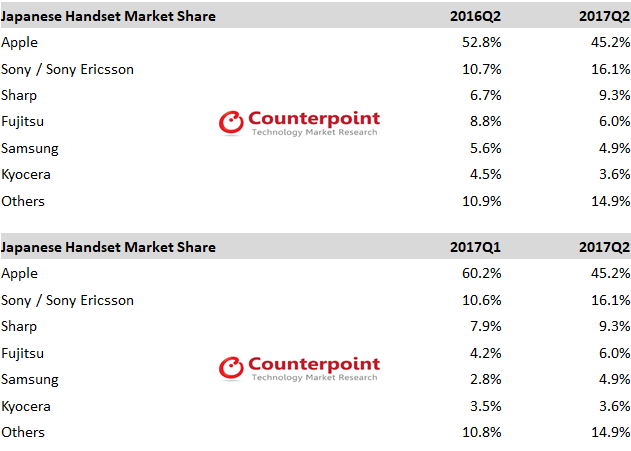






/cdn.vox-cdn.com/uploads/chorus_asset/file/9255767/IC584396.png)
/cdn.vox-cdn.com/uploads/chorus_asset/file/9255775/apple_truedepth.png)


