
The iPhone X: its OLED screen comes from Samsung, whose poor display sales misled analysts. Photo by Aaron Yoo on Flickr.
A selection of 12 links for you. Buying a book will make it better. I’m @charlesarthur on Twitter. Observations and links welcome.
Cryptocurrency-mining malware targeting IoT, being offered in the underground • TrendLabs Security Intelligence Blog
»
Crime follows the money, as the saying goes, and once again, cybercriminals have acted accordingly. The underground is flooded with so many offerings of cryptocurrency malware that it must be hard for the criminals themselves to determine which is best. This kind of malware, also known as cryptomalware, has a clear goal, which is to make money out of cryptocurrency transactions. This can be achieved through two different methods: stealing cryptocurrency and mining cryptocurrency on victims’ devices surreptitiously (without the victims noticing), a process also known as cryptojacking. In this post, we discuss how these two methods work, and see whether devices connected to the internet of things (IoT), which are relatively underpowered, are being targeted.
«
*taps mic* in my book Cyber Wars – published today! – I look at how weak the security around IoT devices tends to be, based on amazingly old code and with terrible business models that don’t envisage security updates.
Cryptocurrency is a quiet way of doing it, rather than the hacking where you get millions of devices to attack someone in a DDOS attack.
link to this extract
China slowdown drags worldwide smartphone market to 2.9% year-over-year decline • IDC
»
smartphone vendors shipped a total of 334.3 million units during the first quarter of 2018 (1Q18), resulting in a 2.9% decline when compared to the 344.4 million units shipped in the first quarter of 2017. The China market was the biggest driver of this decline with shipment volumes dipping below 100 million in the quarter, which hasn’t happened since the third quarter of 2013.
“Globally, as well as in China, a key bellwether, smartphone consumers are trading up to more premium devices, but there are no longer as many new smartphone converts, resulting in shipments dropping,” said Melissa Chau, associate research director with IDC’s Worldwide Mobile Device Trackers. “When we look at it from a dollar value perspective, the smartphone market is still climbing and will continue to grow over the years to come as consumers are increasingly reliant on these devices for the bulk of their computing needs.”
“Despite new flagships from the likes of Samsung and Huawei, along with the first full quarter of iPhone X shipments, consumers looked unwilling to shell out big money for the latest and greatest devices on the market,” said Anthony Scarsella, research manager with IDC’s Worldwide Quarterly Mobile Phone Tracker. “The abundance of ultra-high-end flagships with big price tags released over the past 12-18 months has most likely halted the upgrade cycle in the near term. It now looks as if consumers are not willing to shell out this kind of money for a new device that brings minimal upgrades over their current device. Looking forward, more affordable premium devices might be the solution the market needs in the second half of the year to drive shipments back in a positive direction.”
«
That unwillingness only stretched to companies that weren’t Apple, it seems. Samsung slightly down, Huawei and Xiaomi very much up. “Others” – those outside the top five – way down.
link to this extract
Bloomberg butchers Samsung OLED statements to portray iPhone X as weak • Apple Insider
»
In its latest attack on Apple’s iPhone X, Bloomberg isolated selected statements from Samsung, the exclusive source of the phone’s OLED display panels, and threw out facts that didn’t support its narrative.
Citing mere 3% growth in the company’s Display Panel business segment and a company earnings statement that DP profits “were affected by slow demand for flexible OLED panels,” Bloomberg presented the conclusion that iPhone X sales must be “weak.”
Samsung didn’t say that its Display Panel segment turned in weaker results due to iPhone X. What the company actually reported in its earnings statement for the March quarter was that its DP “OLED Earnings declined due to weak demand and rising competition between Rigid OLED and LTPS LCD.”
It also stated that its DP segment “LCD Earnings stayed flat QoQ thanks to cost reduction efforts and product-mix improvements amid a decline in sales and ASPs caused by weak seasonality.”
So rather than Bloomberg’s contrived messaging portraying that Samsung’s OLED profits were declining because iPhone X was tanking, the reality is that Samsung reported that its entire DP unit was hammered in profitability during the quarter due to intense competition (from other suppliers and from other, cheaper screen technologies) and from weak demand and a decline in sales in general, across both OLED and LCD panels.
«
Samsung’s phone sales were down – despite the launch of the Galaxy S9 and S9 Edge during the quarter. That points to weakness in Samsung’s sales. Odd how people wanted to say that the iPhone X wasn’t selling well. Nobody has said much about the Galaxy S9. It don’t think it’s the hit Samsung might have hoped for.
link to this extract
Blockchain insiders tell us why we don’t need blockchain • FT Alphaville
»
[On Tuesday] a panel of blockchain experts gave evidence on the technology to the British Parliament’s Treasury Select Committee. The panel included Ryan Zagone, director of regulatory relations (yes, that’s apparently really a job title) at Ripple, the company behind the ultimate leap-of-faith-demanding centralised digital currency, XRP.
Mr Zagone gave the committee the usual spiel about the need for a bridging currency for cross-border payments (which we’ve previously debunked). He also told us that 120 financial institutions had signed up to “the Ripple network”. And then he said: “The banks we see on the network are not using XRP. Right now we’re looking down the road at how they can expand their reach through XRP.”
That’s right! No bank is using the digital currency designed for banks. That doesn’t stop it currently being assigned a market value of $32.5bn (more than Twitter’s market capitalisation).
Also on the panel was Chris Taylor, chief operating officer at Everledger, a company that is trying to use the blockchain to track (and miraculously “protect”) diamonds and other assets. Here’s an excerpt from his contribution: “It’s the same as any system – it’s garbage in, garbage out. So you’ve got to make sure that the participants that you’re allowing to contribute to the network are trustworthy.”
He said it, not us. A blockchain is the same as any system. If you feed garbage into it, it will feed garbage back out to you. And if you accidentally feed garbage into it, you can’t change it, because immutability!
Mr Taylor continued: “Blockchain doesn’t solve everything. It doesn’t solve entirely problems that couldn’t be solved in other ways. But we believe blockchain solves the problems that we’re solving in a better way than traditional database technology can provide.”
Compelling stuff, no?
«
Er.. no?
link to this extract
Biohacker Aaron Traywick found dead in a spa • BBC News
»
A biohacker who became infamous after apparently injecting himself with an untested herpes drug in front of an audience has been found dead.
Aaron Traywick’s body had been discovered in a spa room in Washington DC on Sunday, local police said. Vice News reported that Traywick had been using a flotation therapy tank.
The 28-year-old was chief executive of Ascendance Biomedical. He had skirted the law by self-medicating as well as encouraging others to do likewise.
A police spokeswoman has said no evidence has been found to suggest foul play.
Traywick had claimed his biohacking company had developed a DIY “research compound” that could cure HIV, Aids and herpes, but had no independent proof to back this up. Biohacking refers to people’s efforts to alter their own biology by a variety of means including lifestyle and diet changes, surgery and the use of unlicensed therapies.
The BBC challenged Traywick over his behaviour when it interviewed him at the BodyHacking Con in Austin, Texas, in February. Traywick, who had herpes, had performed a stunt at the event, apparently injecting his company’s unregulated product into his leg. On stage, he had referred to the product as a “research compound”.
But in conversation with the BBC he described it as a “treatment” – a claim that had the potential to attract the attention of the US Food and Drug Administration.
«
An autopsy has been carried out, but not released so far.
link to this extract
Fitbit’s current-quarter revenue forecast misses estimates • Reuters
»
Wearable device maker Fitbit Inc’s forecast for current-quarter revenue missed Wall Street estimates, hurt by a drop in sales of fitness trackers.
Shares of the company fell 1.6% to $5.41 in after-market trading on Wednesday after the company said it expects a 19% drop in the second-quarter revenue.
The company said it sold 2.2m devices in the quarter at an average selling price of $112 per device, below analysts’ estimate of 2.33m devices, according to financial data analytics firm FactSet.
Fitbit said it expects revenue for the current quarter to be in a range of $275m to $295m, below analysts estimate of $309.9m, according to Thomson Reuters I/B/E/S.
In April, Fitbit announced the worldwide launch of its latest smartwatch ‘Versa’ after Chief Executive Officer James Park promised to launch a more ‘mass appeal watch’ in 2018 compared with ‘Iconic’, the company’s first smartwatch that had failed to impress.
«
You have to go back to 2014 to find such a low number of devices sold. Revenue fell 18%. It’s only a matter of time before it gets rolled up by someone like Google (which needs a wearables business that actually works for it, unlike WearOS).
link to this extract
‘Success’ on YouTube still means a life of poverty • Bloomberg
»
Do your children dream of YouTube stardom? Do them a favor: crush that ambition now.
New research out of Germany billed as among the first to review the chances of making it in the new Hollywood shows a vanishingly small number will ever break through—just like in the old Hollywood.
In fact, 96.5% of all of those trying to become YouTubers won’t make enough money off of advertising to crack the US poverty line, according to research by Mathias Bärtl, a professor at Offenburg University of Applied Sciences in Offenburg.
Breaking into the top 3% of most-viewed channels could bring in advertising revenue of about $16,800 a year, Bärtl found in an analysis for Bloomberg News. That’s a bit more than the U.S. federal poverty line of $12,140 for a single person. (The guideline for a two-person household is $16,460.) The top 3% of video creators of all time in Bärtl’s sample attracted more than 1.4 million views per month.
«
But as The Outline points out (amalgamating various sources), those YouFaceInstaTubeGramBookers can make money on the side – by promoting crap and getting paid for it.
link to this extract
Revealed: how bookies use AI to keep gamblers hooked • The Guardian
»
Current and former gambling industry employees have described how people’s betting habits are scrutinised and modelled to manipulate their future behaviour.
“The industry is using AI to profile customers and predict their behaviour in frightening new ways,” said Asif, a digital marketer who previously worked for a gambling company. “Every click is scrutinised in order to optimise profit, not to enhance a user’s experience.”
“I’ve often heard people wonder about how they are targeted so accurately and it’s no wonder because its all hidden in the small print.”
Publicly, gambling executives boast of increasingly sophisticated advertising keeping people betting, while privately conceding that some are more susceptible to gambling addiction when bombarded with these type of bespoke ads and incentives.
Gamblers’ every click, page view and transaction is scientifically examined so that ads statistically more likely to work can be pushed through Google, Facebook and other platforms…
…“I never cease to be amazed at how low the gambling industry is prepared to go to exploit those who have indicated an interest in gambling,” says Carolyn Harris, a Labour MP who has campaigned for gambling reform.
“The industry is geared to get people addicted to something that will cause immense harm, not just to society but to individuals and their families. They are parasitical leeches and I will offer no apology for saying that.”
«
Completely agree with Harris.
link to this extract
The myth that civilian gun ownership prevents tyranny • ThinkProgress
»
In assessing data from 2008-2018, civilian gun ownership rates appear to have no influence on the strength of a country’s democracy.
For instance, five of the six countries with the greatest democratic improvements over the past decade are located among the bottom half of countries in terms of civilian arms rates. At the same time, six of the 11 countries with the greatest democratic backsliding have also been in the bottom half in terms of gun ownership rates. (For Freedom House, a lower score on its democracy index is better in terms of democratization; those with the highest scores are considered dictatorships.)
Look at Fiji and Ethiopia, for instance. In 2008, both had identical Freedom House scores, with nearly identical civilian arms ownership rates (Fiji has 0.5 guns per 100 civilians, while Ethiopia has 0.4). But a decade later, Fiji was far freer, boasting democracy scores comparable to Colombia and Montenegro, whereas Ethiopia was suffering under a far bloodier regime than it is now, scoring worse than dictatorships like Kazakhstan and Belarus.
«
Ten years seems quite a short timespan for such a study. You could probably take it over 100 years and see much the same results, though. But it gives the lie to the US suggestion that you need people to have guns so they can fight off the government:
»
The Second Amendment did little to prevent American governments from creating internment camps for Americans of Japanese descent or from enacting Jim Crow laws, repeatedly calling the country’s claims to liberal democracy into question. “White supremacists are absolutely correct in pointing to the Second Amendment as having been created for their supremacy in perpetuity, so that what they regarded as ‘tyranny’ was and is any deviance by government from that arrangement,” Roxanne Dunbar-Ortiz, the author of Loaded, a recent history of the Second Amendment, told ThinkProgress.
«
Building successful online communities: Evidence-based social design • AcaWiki
»
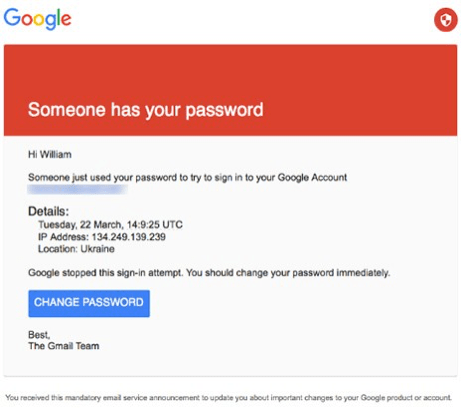
The authors also suggest that ascribing blame or community sanctions may be less effective than offering community members a way to “save face” “without having to admit that they deliberately violated the community’s norms.” They describe a system called stopit designed at MIT to address computer-based harassment. When users reported harassment, the system sent a message to the alleged harasser claiming that the alleged harasser’s account may have been compromised and urging them to change their password. Here is the rationale given by Gregory Jackson, the Director of Academic Computing at MIT in 1994:
»
recipients virtually never repeat the offending behavior. This is important: even though recipients concede no guilt, and receive no punishment, they stop. [this system has] drastically reduced the number of confrontational debates between us and perpetrators, while at the same time reducing the recurrence of misbehavior. When we accuse perpetrators directly, they often assert that their misbehavior was within their rights (which may well be true). They then repeat the misbehavior to make their point and challenge our authority. When we let them save face by pretending (if only to themselves) that they did not do what they did, they tend to become more responsible citizens with their pride intact.
«
«
That is amazing. You’d need a ton of “you’ve been hacked” warnings to make Twitter calm down, but worth a try, huh?
link to this extract
Pentagon orders stores on military bases to remove Huawei, ZTE phones • WSJ
»
The Pentagon is moving to halt the sale of phones made by Huawei Technologies and ZTE in retail outlets on US military bases around the world, citing potential security threats they say the devices could pose.
The move intensifies a squeeze the Trump administration has put on the two Chinese makers of telecommunications gear and mobile devices. Washington officials have said Beijing could order Chinese manufacturers to hack into products they make to spy or disable communications. Huawei and ZTE have said that would never happen.
Huawei is the world’s third-largest smartphone maker, behind Apple and Samsung Electronics, but it sells very few devices stateside. ZTE, however, is the fourth-largest seller of phones in the US, with a 9.5% share of units shipped, according to research firm IDC.
“Huawei and ZTE devices may pose an unacceptable risk to the department’s personnel, information and mission,“ said Army Maj. Dave Eastburn, a Pentagon spokesman, in a statement. “In light of this information, it was not prudent for the department’s exchanges to continue selling them.” He was referring to the retail outlets at or near military installations in the US and overseas that cater to American soldiers and sailors. Only 2,400 Huawei and ZTE phones were sold at those outlets last year, he said.
«
Such drama, until that last sentence. It’s more about the perception on this. However, the earlier US embargo on ZTE in particular is going to hurt it: 9.5% of the US market is a big slice to lose (as seems likely).
link to this extract
Intel kills Kaby Lake-X, the bizarre enthusiast CPUs that nobody wanted • PCWorld
»
Intel’s Kaby Lake-X chips were a headscratcher from the start.
Launched alongside the massively multi-core Skylake-X processors last summer, the quad-core chips didn’t offer any noticeable advantages over standard Kaby Lake chips beyond a very slight speed bump. Yet they required pricey X299 motherboards that cost significantly more than mainstream hardware—then failed to take advantage of the key platform advantages of the swankier chipset. Intel pitched the CPUs as an overclocker’s dream, but really, they were just plain weird, and effectively made obsolete mere months after release with the introduction of the 6-core, 12-thread Core i7-8700K in October.
Now Kaby Lake-X is officially obsolete. As first noticed by Tech Report, Intel quietly discontinued the Core i5-7640X and Core i7-7740X in a new document outlining end-of-line dates for the chips (PDF). The paperwork hints that Kaby Lake-X was indeed supplanted by 8th-gen Coffee Lake CPUs, stating that “Market demand for the products listed in the ‘Products Affected/Intel Ordering Codes’ tables below have shifted to other Intel products.”
«
Intel’s processor line has just exploded, Cambrian-style, and is now being trimmed back. One hopes.
link to this extract
Errata, corrigenda and ai no corrida: none notified
You can sign up to receive each day’s Start Up post by email. You’ll need to click a confirmation link, so no spam.






/cdn.vox-cdn.com/uploads/chorus_asset/file/10715051/DblEn82X4AA9KZd.jpg)