Seen Skyfall? Remember the scene when we first encounter Javier Bardem playing whoever the baddie is? Here it is, as a reminder:
Bear it in mind. We’ll come back to it.
So: Ben Bajarin had some pretty bleak news for top-end Android smartphone companies recently:
High end Android shipments ($500 and above) have decreased from ~ 280m units in 2012 to ~ 190m units in 2015. Curse of modular..
— Ben Bajarin (@BenBajarin) February 5, 2016
That’s a decline of 90m, even while the overall smartphone market has grown from 704m (of which 501m were Android) to 1.43bn (of which 1.16bn were Android).
But your objection is probably the same as mine: isn’t the decrease in those sur-$500 shipments because the price of high-end Android handsets has fallen? The price you have to pay to get something with the same qualities as the $500-or-more Android flagship is lower than it was in 2012.
This is almost certainly true – but it isn’t much compensation for those struggling to expand their sales and seeing average selling prices (ASPs) fall. There’s a simple financial reason: if you keep selling the same number of phones at lower ASP, your profit will inevitably fall off a cliff as fixed costs such as staff and administration weigh you down.
What’s also notable that Apple hasn’t – so far – been affected by any drop in ASP. Since the start of 2010, its ASP for any quarter has only been below $600 four times – and in the most recent quarter, it reached an all-time high. Which leads one to wonder: what the hell is going on? But let’s show you the numbers from the quarter, and then discuss them.
| Q4 2015: the smartphone scorecard * denotes estimate: explanations below |
|||||
| Company | Handsets (million) |
Revenues | Handset ASP |
Operating profit |
Per-handset profit |
| Samsung | 81.5 | $20.40bn | $225.39 | $1.90bn | $23.29 |
| Apple | 78.25 | $51.64bn | $690.50 | $14.41bn* | $184.10* |
| LG | 15.3 | $3.22bn | $210.26 | –$51.47m | –$3.36 |
| Sony | 7.6 | $3.20bn | $421.58 | $198.91m | $26.17 |
| HTC | 3.4* | $0.81bn | $237.05 | –$128.00m | –$37.65 |
| Microsoft Mobile |
4.5 | $0.84bn | $185.70 | –$162m | –$36.11 |
Assumptions
Samsung: featurephones (it sold 18.5m) had an ASP of $30, and generated zero profit; its tablets had an ASP of $100 and generated zero profit. (These are the same assumptions as in previous quarters. If the ASP is lower, then revenues are higher and the ASP of smartphones is higher; if profits are non-zero on tablets and featurephones, profits on smartphones are lower.)
Apple: operating profit has to be assumed, at the same 27.9% share of revenue as in previous quarters. This may not be true – new phones such as the 6S/Plus are more expensive to produce at the start of a cycle (such as now). But again, consistency probably helps give the broad picture rather than trying to dive into numbers that only a few people inside Apple truly know.
Microsoft Mobile: assumes, as previously, that featurephones (there were 22.5m of them) had an ASP of $15 and gross margin – the profit purely on the goods, not including costs such as R+D and administration etc – of $5. These are the same assumptions as in the past. I’ve chopped the estimates of R+D and administration cost from $200m in previous quarters to $100m and from $300m to $100m because Microsoft said in its 10-Q that
Operating expenses [in the Devices division, which makes the Surface Pro, Surface Book, and phones] decreased $561m or 14%, mainly due to lower sales and marketing expenses and research and development expenses. Sales and marketing expenses decreased $359m or 18%, driven by a reduction in phone expenses, partially offset by marketing expenses associated with the launch of Surface Pro 4, Surface Book, and Windows 10. Research and development expenses decreased $179m or 11%, mainly due to a reduction in phone expenses.
To reach my figure for Microsoft’s profitability (or lack of it) I’ve taken $300m out of the Microsoft phone group’s operating costs, which might be close to the amount from the total $920m it says it cut. Without more clarity (or a shutdown of the phones division), hard to tell. But there’s no way one can see a division which sells 4.5m phones and generates around $830m being profitable; that’s about the same scale as HTC, which we know is not profitable because it publishes its results.
Microsoft has become increasingly opaque about the profitability of its phone side (though of course Apple has never declared any numbers there; one has to back it out from what is known about Mac and iPod profitability).
Where’s Android Wear?
You may ask yourself: where are Android Wear shipments as a factor in the revenues of LG, Sony or Lenovo (or Samsung’s Gear in its figures)? To which I’ll answer: don’t worry. Too small to trouble with. By my calculations, and those of other analysts, Android Wear shipments from all makers in Q4 totalled 0.9m. At around $150 each, that’s a rounding error in revenue for any of these players. (I’ll revisit my ongoing calculations on Android Wear usage figures in the near future.)
Handset pricing: Apple stands on the precipice
The real lessons of what’s going one here aren’t easy to see from a single quarter’s numbers. But if you want it in a single statistic, look at the contrast between Sony and LG. LG sold nearly twice as many phones, but Sony made a respectable profit, while LG made a loss. What’s the difference between them? ASP. Sony’s phones sold at an average price of $421.58, while LG’s were half that – $210.26. (This doesn’t mean that every LG phone sold at that price, or every Sony phone. But it tells you that Sony must have sold a lot more expensive phones than LG.)
Graph the trend in ASP and it becomes clearer: Sony has (as it said it intended to) driven up ASP, while LG has been pushed down.
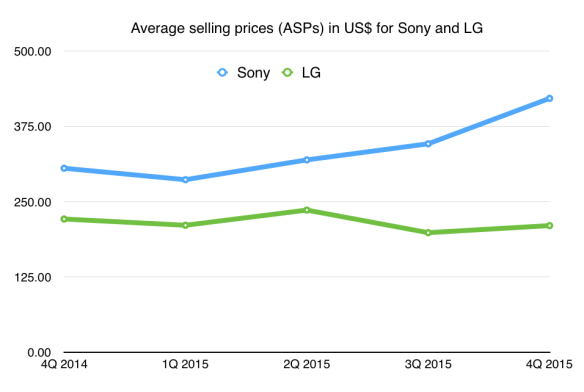
Sony’s overall phone ASP has risen (though it now only sells half as many phones as LG)
Sony is literally the only Android OEM which has managed to raise ASPs consistently over the past year, and after a lot of pain (in the form of losses) it seems to be paying off in the form of profit. There’s a simple reason why, of course. The higher the price you can sell something for, the lower the proportion of your revenues the fixed costs – sales, administration, staff, and even seemingly trivial things like patent licensing – become. If you can drive your price up, you begin making profit. But if your ASP is driven down, everything starts eating into the bottom line.
Sony’s problem though is that it’s shrinking year-on-year. After a while, if your shipments are too low then even a high ASP can’t save you from your fixed costs – see HTC for the example. Still, Sony stands alone as having the highest ASP among Android OEMs. That doesn’t mean it sells the largest number of pricey handsets (Samsung surely has that title) but that it is consistently high.
Note how it’s only Samsung, which has both chip foundries and screen fabrication facilities, that has consistently been the biggest smartphone OEM and the only consistently profitable Android OEM.
But Samsung’s ASP is coming down quarter after quarter; it’s only keeping its profits level by making more phones, whose ASPs are falling. That hits revenues and profits – as charted below.

Note also how the total number of handsets that Samsung, HTC, Sony, LG and Lenovo/Motorola sold in 4Q15 was down to 128m, compared to 133.15m a year before – a fall of 4% while the smartphone business as a whole grew 6%. There’s a growing squeeze on the top end Android business, which we’ve seen since Q2 last year.
Apple meanwhile officially stayed static, mainly by “stuffing the channel” – getting carriers and others to buy phones which hadn’t reached customers by the end of the quarter, but counted as “shipped”; about 3m were pushed that way. This means Apple’s numbers of shipments to customers probably rose only minimally to 75m. Gartner’s figures say that Apple’s sales to end customers actually fell.
But there’s a bigger dynamic going on. Philip Elmer-DeWitt posted a fun interactive graphic showing how Android ASPs have moved compared to those for the iPhone. Here, statically, is the data – which comes from IDC and covers all Android handsets, of course, not just those at the top end from the companies which publish public figures:
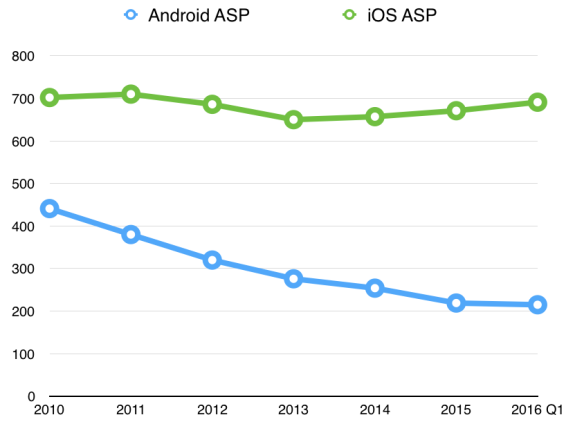
In US$, iPhone average prices are remaining high; Android prices are falling as its base grows
The growing gap (or “delta”) between those two is dramatic. Of course part of that is what’s happening as Android reaches more and more people in the world: the poor in Kenya can’t afford an iPhone, but they can probably afford a $50 (Android) smartphone if it will help them do their jobs better. So is this just about Apple hanging on to profits as is often suggested? Not at all, responded Horace Dediu:
@philiped Common misconception. Apple is not concerned with keeping profits. It’s concerned with prices. Within the price is perception.
— Horace Dediu (@asymco) February 15, 2016
“Within the price is perception.” It’s quite the observation. As Dediu also pointed out, Apple hasn’t changed the selling price of its Mac line of computers for around 20 years. For all that Apple’s prices seem out of reach, that is precisely its attraction to some people – perversely, in the view of those who see smartphones (and PCs) as utterly functional and interchangeable. To some, they really aren’t.
And to continue having that perception, Apple also has to stand apart with its operating system and services. It could never license iOS; and I don’t see how it could make iMessage cross-platform without diluting its brand value. (That doesn’t mean it couldn’t grow iMessage into a messaging platform in its own right, able to do payments and so on.)
The pricing gap
With Android phones getting cheaper all the time, there’s not a lot of hope for the former premium makers. Kantar ComTech posted a neat graphic showing how the torch is passing among Android users in the EU’s five largest countries (Germany, UK, France, Spain, Italy) which shows this starkly:
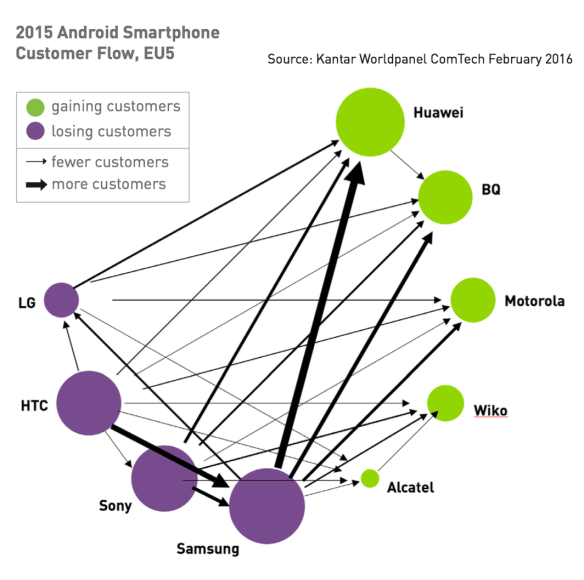
Owners are abandoning established Android OEMs (purple) for rivals (green). Source: Kantar.
You’ve probably heard of Huawei, but would you have picked Alcatel or those others as rivals to Samsung or HTC? Probably not, even a few quarters ago.
LG is trying to escape this by effectively making this year’s G5 flagship modular, with add-ons such as cameras, high-end audio DAC and VR systems that you can plug in. The idea is to make the G5 more attractive because it has these extras. However given the numbers of G5s it’s likely to sell (a few million?) those add-ons (called “Friends”) are likely to be stranded. (I remember the same with Handspring’s add-ons. Great idea, but commercially doomed.) It’s extra revenue, and possibly each Friend sold will generate as much profit as a phone – accessories can do that – but won’t push up the ASPs of the actual phone. And if Friends are made available for cheaper LG phones, why would you buy the flagship when you can get the extra functionality of a Friend for cheaper?
Samsung has in effect already cut the price of the S7 by offering a free VR system to anyone who pre-orders. And Sony has Osborned its existing products with its announcements at Mobile World Congress, which its high-end customers will have noticed.
None of this helps with the finances, or fights off the rise of cheaper, just-as-good devices running the same software.
The Android handset market is broadening, and deepening, like a pothole opening up beneath the previoiusly established companies. Xiaomi (VC-funded), Huawei (big network business throwing off cash), scores of tiny Chinese OEMs, niche makers… they’re all eating away at the edge of what seemed like a certain market.
And add to that the slowdown in the smartphone market, and you have a recipe for a repeat of that rat pit we saw referred to way back at the top. It’s going to be last man, or OEM, or if you prefer rat, standing.
Looking down from the precipice into the rat trap
But what does Apple do in all this? The gap between its average price and that of the “average” Android phone is widening all the time. Isn’t that a problem? A big one?
Yet Apple’s brand, and that position, isn’t built on hardware alone. You don’t hear about people using an iPhone in spite of iOS, the way you do about Samsung and its TouchWiz skin, for instance. iOS’s software reputation remains pretty solid: it hasn’t, despite many predictions, lost its lead in getting apps before Android in the west. (As a reminder, Eric Schmidt’s “in six months developers will be writing for Android first” promise was in December 2011; didn’t work out, at least in the west. Asia was and remains Android-first for most things.) iOS 9’s adoption was faster than iOS 8, despite the ecosystem being bigger. Apple Music seems to be winning users, though it’s a long, long way behind Spotify, especially on Android.
The question of how Apple can maintain its pricing in the face of the rampant deflation in the Android handset market remains the most interesting one around. Yet it has managed that in the PC market: its ASP there is $1200, while that for the “big” PC makers ranges from $300 (Acer) to $500 (Lenovo). And it has managed that for more than a decade. But it’s done that as a niche product which has only recently become more mainstream. In the phone market, its share of all handsets in Q4 was over 10%, and 19% of smartphones. Can you maintain premium pricing and be mainstream?
For the Android OEMs, though, the story remains the same: you’re down there in the rat trap, and that curious face above you gazing down is Javier Bardem, waiting to see who’ll be left at the end. And I’m just behind, looking over his shoulder, just as fascinated.